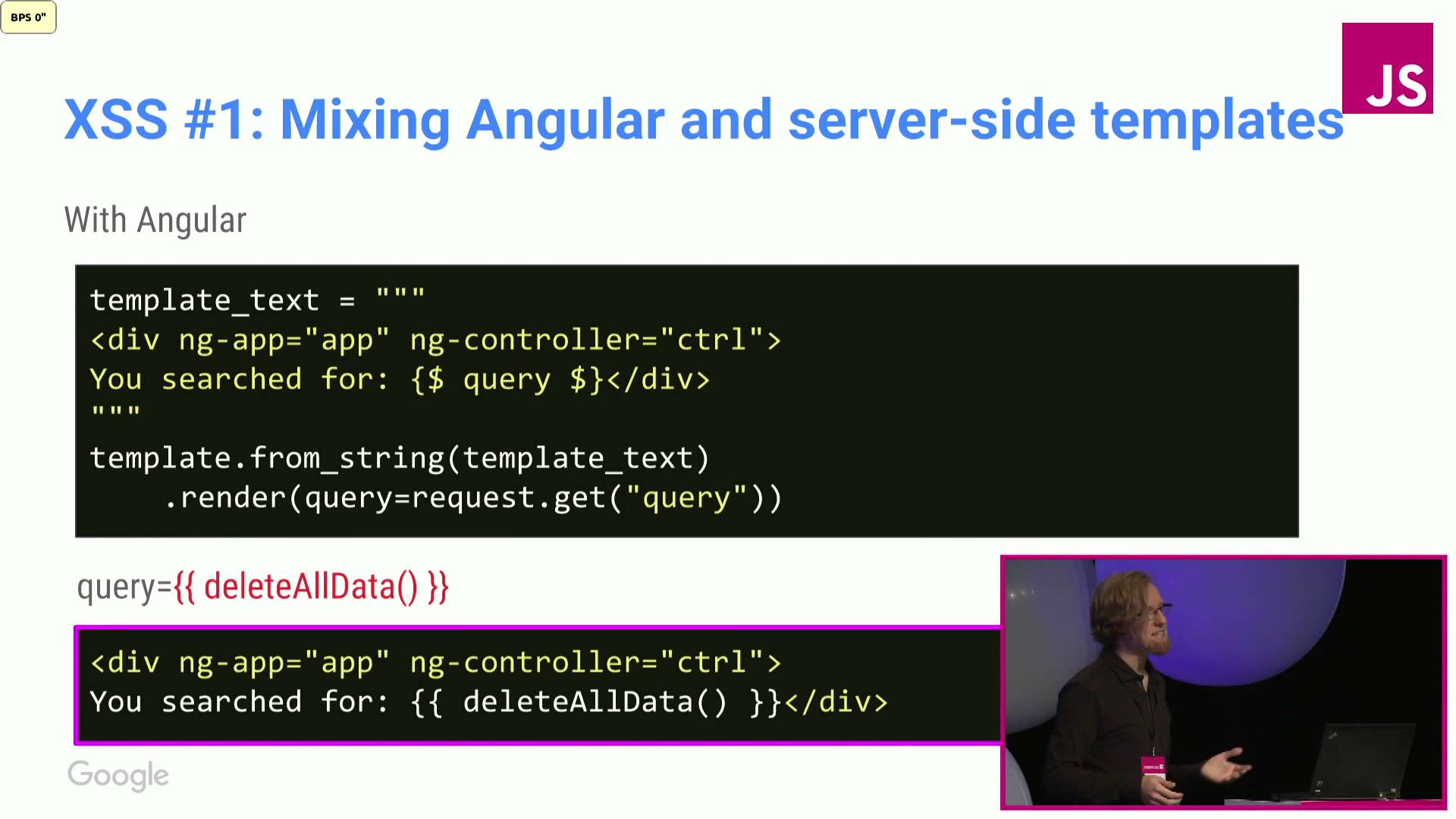
In the recent years high-level frameworks have become the de facto standard for writing client-side webapp code. Angular, Polymer, or Dart all provide extremely useful abstractions for building applications, but also indirectly expose rough edges of the web platform which often lead to vulnerabilities (e.g. XSS).
In my talk I will provide a security engineer’s perspective on some of the common pitfalls which tend to affect code written using such frameworks based on real examples of bugs in Google apps. I will also explain why security reviews of such apps are often more difficult to conduct than those of “bare metal” JS code, what could be done to fix this, and why framework designers should care about it.