The Tesla Model S is the most connected car in the world. It might surprise you to hear that it is also one of the most secure. In this talk we will walk you through the architecture of a Tesla Model S noting things that Tesla got right as well as identifying those that they got wrong. From this talk you will get an intimate understanding of how the many interconnected systems in a Tesla model S work and most importantly how they can be hacked. You will also get a good understanding of the data that this connected car collects and what Tesla does with this telemetry. We will also be releasing a tool that will enable Tesla Model S owners to view and analyse that telemetry in real time. Finally we will also be releasing several 0day vulnerabilities that will allow you to hack a Tesla Model S yourself – both locally and remotely. Note – only one of the 6 vulnerabilities we will discuss and release has been fixed. Disclaimer: With great access comes great responsibility – In other words we are not responsible for any Tesla Model S bricked by over enthusiastic attendees of this talk :)
Videos & Talks
Artur Janc: Security in the world of JS frameworks
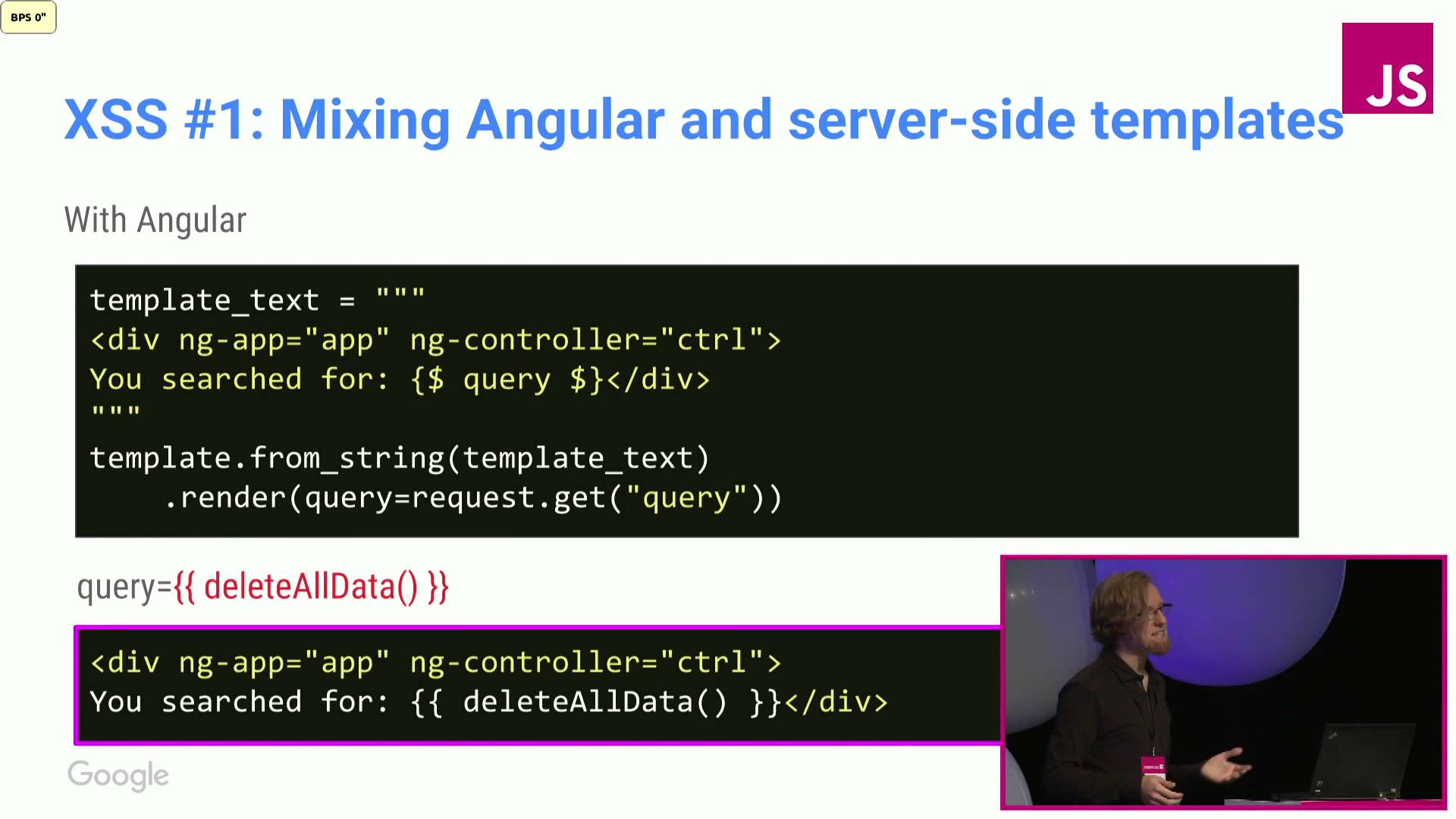
In the recent years high-level frameworks have become the de facto standard for writing client-side webapp code. Angular, Polymer, or Dart all provide extremely useful abstractions for building applications, but also indirectly expose rough edges of the web platform which often lead to vulnerabilities (e.g. XSS).
In my talk I will provide a security engineer’s perspective on some of the common pitfalls which tend to affect code written using such frameworks based on real examples of bugs in Google apps. I will also explain why security reviews of such apps are often more difficult to conduct than those of “bare metal” JS code, what could be done to fix this, and why framework designers should care about it.
Malware Hunting with the Sysinternals Tools
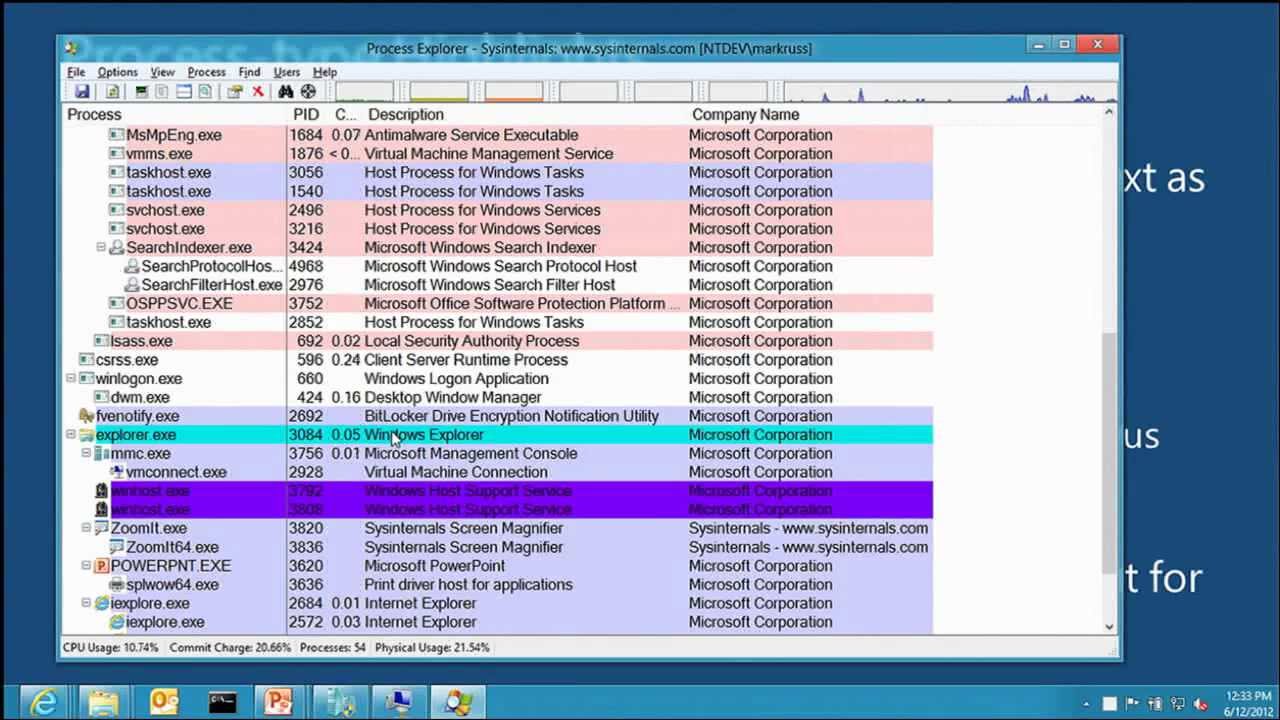
This session provides an overview of several Sysinternals tools, including Process Monitor, Process Explorer, and Autoruns, focusing on the features useful for malware analysis and removal. These utilities enable deep inspection and control of processes, file system and registry activity, and autostart execution points. Mark Russinovich demonstrates their malware-hunting capabilities by presenting several real-world cases that used the tools to identify and clean malware, and concludes by performing a live analysis of a Stuxnet infection’s system impact.
Marshalling Pickles – Chris Frohoff & Gabriel Lawrence – OWASP AppSec California 2015
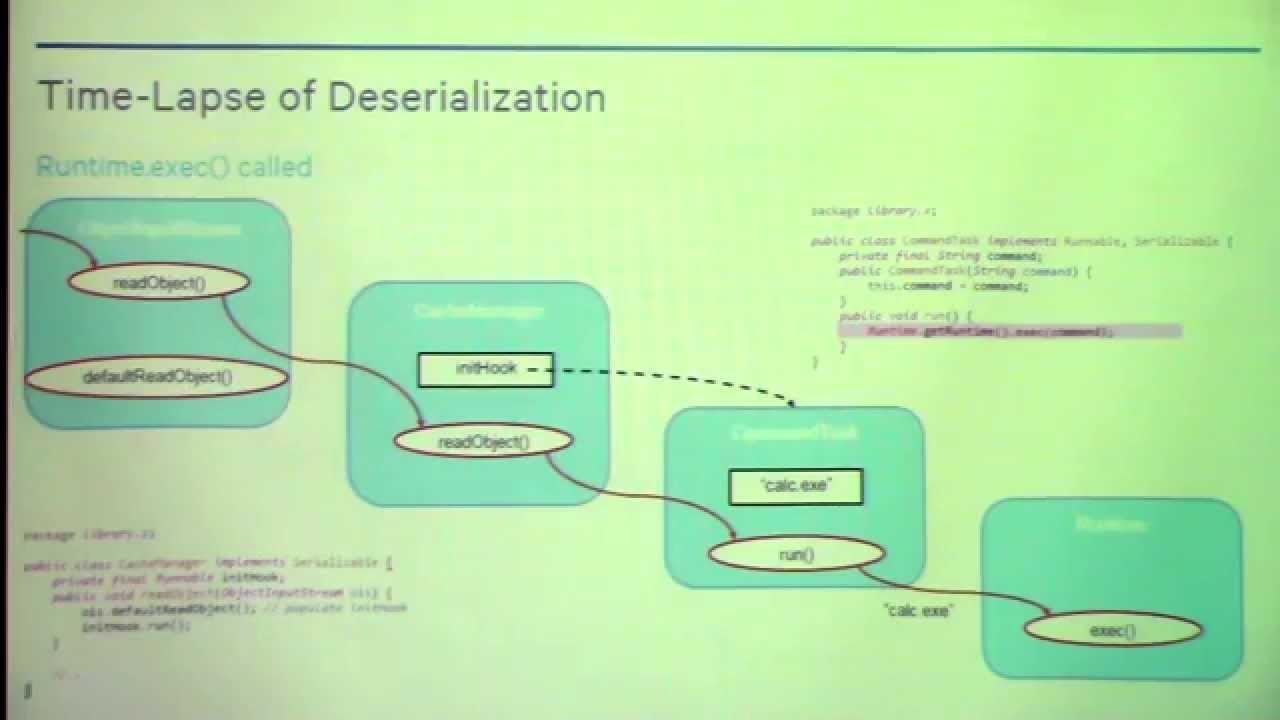
Object serialization technologies allow programs to easily convert in-memory objects to and from various binary and textual data formats for storage or transfer – but with great power comes great responsibility, because deserializing objects from untrusted data can ruin your day. We will look at historical and modern vulnerabilities across different languages and serialization technologies, including Python, Ruby, and Java, and show how to exploit these issues to achieve code execution. We will also cover some strategies to protect applications from these types of attacks.