Hello
I discovered interesting XSS attack vector on NameCheap firm. As you know, you can sign your certificates via NameCheap.
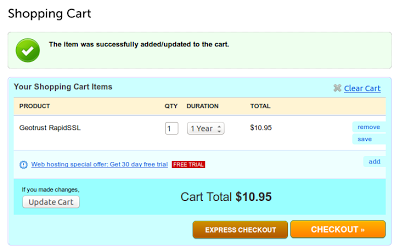
Vulnerability
Lets buy new one SSL certificate.
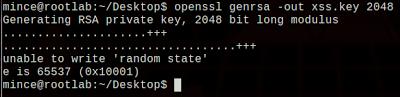
Following part is important side of my finding. Because we’ll put our payload inside of CSR file.
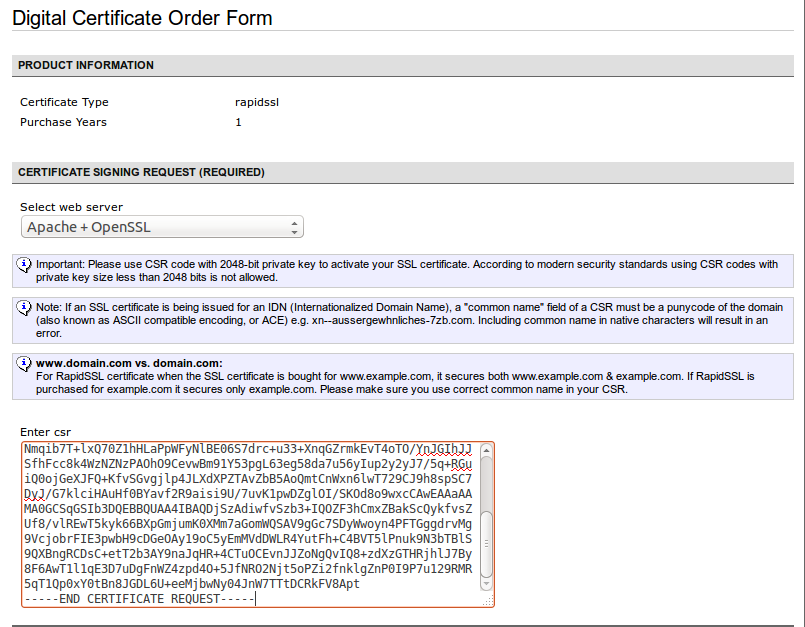
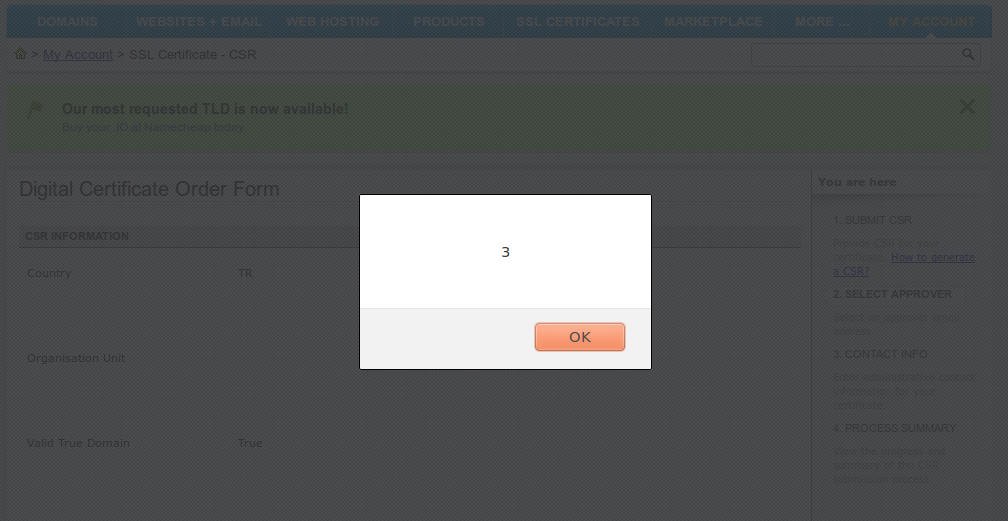
Next step is generate CSR file from our SSL key. Please pay attention to next picture. You’ll see our XSS payloads at inside of the certificate file’s variables like Organization name, Locality Name and so on.
We’ll put content of that file into the NameCheap web form in order to sign it by authority.
NameCheap will parse that content and grab some field from our CSR file which contains XSS payloads in some fields.
I don’t know how can we use that vulnerability as an attack vector. But we usually hide payload at inside of POST, GET, COOKIE or even USER-AGENT but I’ve never experienced something like that before.