Tuleap is a full free Open Source Suite for Application Lifecycle Management. Traditional development, Requirement Management, Agile Development, IT Service management… Tuleap makes software projects more productive, collaborative and industrialised.
Summary of the reported vulnerabilities:
Vulnerability A: SQL injection
Confirmed and reproduced
Severity: High
CVSS v3 base score: 8.8 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H)
Resolution status: Fix integrated into Tuleap 8.19.99.2 (commit 7333184217e2dd880259d3bb2c42af6541ed8737)
Vulnerability B: Reflected Cross-Site Scripting
Confirmed and reproduced
Severity: Medium
CVSS v3 base score: 6.1 (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
Resolution status: Fix integrated into Tuleap 8.19.99.5 (commit 38d20046d9796a987168b4fccafae9ef2725ed6e)
Vulnerability C: Reflected Cross-Site Scripting
Confirmed and reproduced
Severity: Medium
CVSS v3 base score: 6.1 (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
Resolution status: Fix integrated into Tuleap 8.19.99.1 (commit b07641eda8e98acf896fce2304d771848ef1451a)
A – SQL Injection
Following screenshot is taken from tuleap-8.18/src/www/widgets/updatelayout.php file which is accessible for users. updatelayout.php is responsible for user dashboard view configuration. You can use different type of seperation such as 2 columns, 3 columns or Left menu.
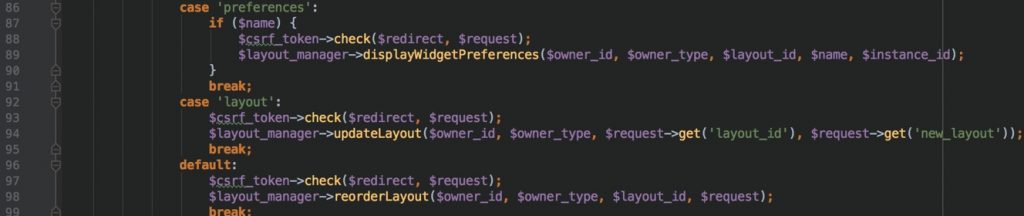
Line 94 will be executed when user input action is layout. updateLayout() function which belongs to LayoutManager class takes 5 different function parameters.
First parameter ($owner_id) is coming from session and it’s integer number.
Second parameter ($owner_type) is coming from substr($request->get(‘owner’), 0, 1) function result. Even it’s coming from user input, Tuleap takes first character of it. That means first two parameter is immune to SQL Injection attack.
4th and 5th parameters is taken directly from client and used as a function parameter without validation.
Following codes are belongs to the updateLayout() function which is member of WidgetLayoutManager class.
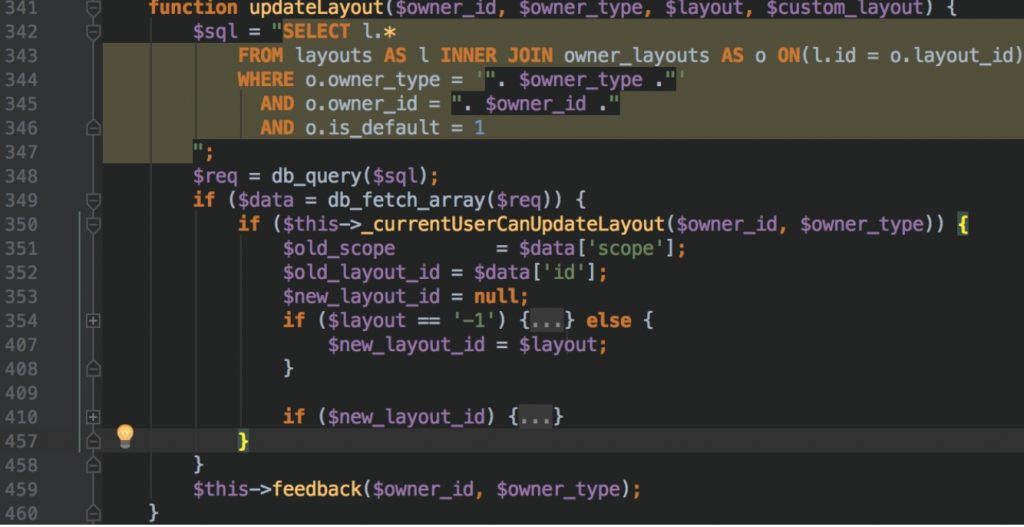
The function executes sql query at the beginning and it use $owner_id and $owner_type during query building stage.
Line between 350 – 458 will be activated if there is a returned data from execution. Between these lines Tuleap checks current user privileges in order to be sure that operation can be taken from user who send HTTP request. And then workflow will be changed depending on $layout and $new_layout_id variables.
We know that $layout is a function parameter and it’s totally under the client control. Also it’s not validated before used as a function parameter. On line 354 says that if $layout is not a -1 then $new_layout_id equals to $layout. That means we can also take control of $new_layout_id parameter as long as $layout is not minus one!
Here is the what happens when $new_layout_id exist. Another saying, $layout is not minus one.
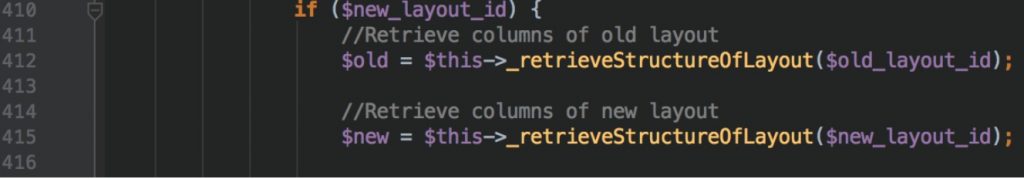
There is two function call. First one takes $old_layout_id as a parameter and second one takes $new_layout_id. Let’s go be previous screen shot and look at line 352. $old_layout_id will be defined when $layout equal -1 and value will be coming from database. There is no way to take control of $old_layout_id at first glance.
As a result of these informations, we decided to with $new_layout_id. Now it’s time to look at _retrieveStructureOfLayout() function definition.
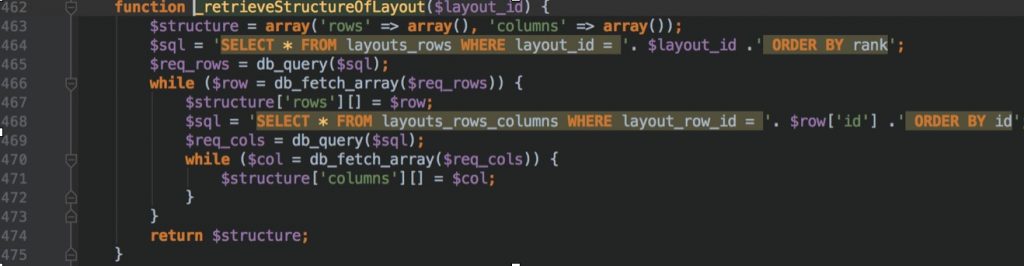
Bingo..! $layout_id is used during sql query building without PDO nor escaping.It is a time-based sql injection vulnerability.
Steps to Triggering Vulnerability
- Register a user. Only registered users can change their layout.
- Set action to layout
- Place your SQLi payload to the layout_id input. That means $layout variable of updateLayout() function will not equal to -1. When this condition returned false, “else” section will be execution and then $layout variables become $new_layout_id.
- $new_layout_id will be used as a _retrieveStructureOfLayout() function parameter.
- Sql injection.
PoC
- In order to reach vulnerable module, please following these instruction.
- Open HomePage (https://10.0.0.134/my/)
- Choose – “Customize widgets” button located top left of the page.
- Select “Cusomize layout” section of.
- Select “3 columns” anything you want.
- Intercept HTTP request and change layout_id variable with 1 or sleep(50) # or 1 or sleep(50)— . # or double dash used for omitting ‘ ORDER BY rank’ operation that appended by Tuleap during query building.
- Response will be returned around after 1 minute.
B – Reflected Cross-Site Scripting
Following codes are taken from src/www/svn/index.php
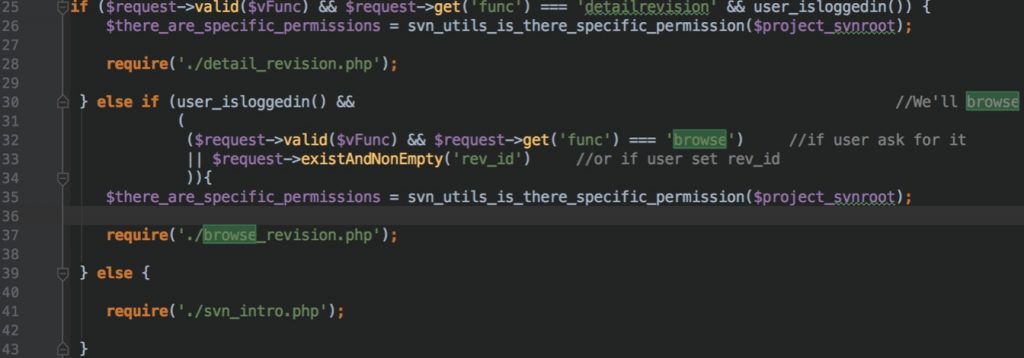
func is under the client control. When it equals to the browse Tuleap includes browse_revision.php file.
Following screenshot is taken from browse_revision.php file. Please look at line 237 and 238. You will see that $_path and $_srch variables are used during HTML content generation with purify() .
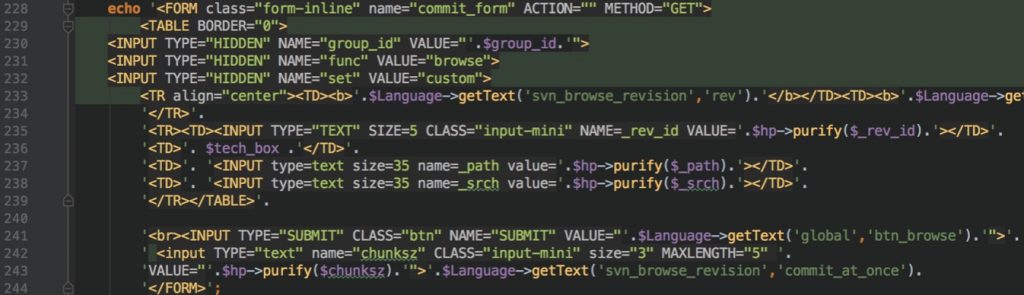
We know that purify is responsible for variable encoding in order to mitigate XSS issues. But there is a one tiny mistake that causes very huge problem.
Lets say $_srch variable is INVICTUS. Then following HTML content will be generated on line 238.
<TD><INPUT type=text size=35 name=_srch value=INVICTUS></TD>
VALUE attribute doesn’t have quotes..! That’s can be very hard to see when php and html codes are mixed on files.
Encoding libraries usually encodes context escaping characters such as ‘ or “ or < etc. But when quotes aren’t used for HTML attributes then browsers will use SPACE as a separator. Let’s say ;
$_srch = X onmouseover=alert(1)
Then result gonna be like this.
<TD><INPUT type=text size=35 name=_srch value=X onmouseover=alert(1)></TD>
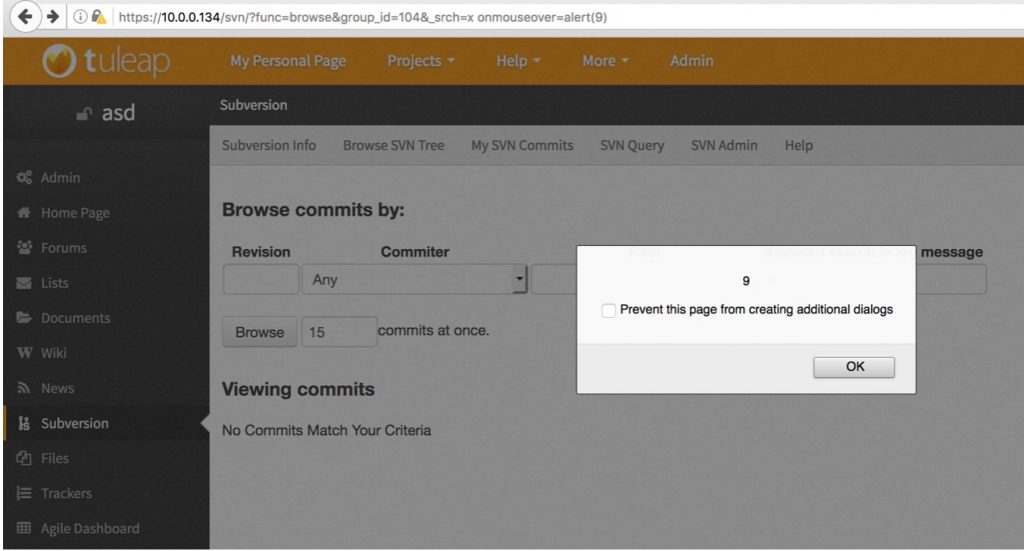
PoC
https://10.0.0.134/svn/?func=browse&group_id=104&_srch=x%20onmouseover=alert(9)
C – Reflected Cross-Site Scripting
Following source code belongs to src/www/admin/grouplist.php file. User controlled data it taken from client through status variable is used for $export variable. And then $export variable is being used during HTML code generation without encoding.![]()
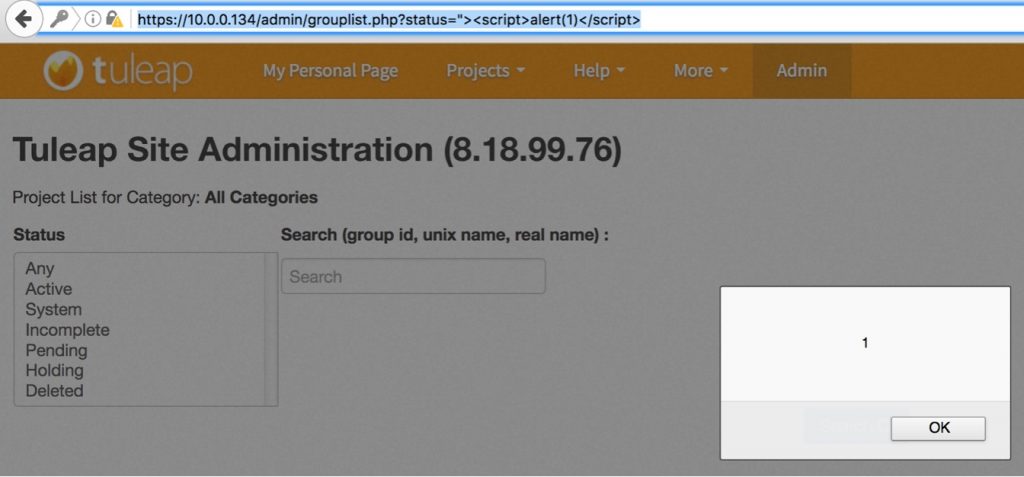
PoC:
https://10.0.0.134/admin/grouplist.php?status=%22%3E%3Cscript%3Ealert(1)%3C/script%3E
Timeline:
16 September 2016: First contact with Vendor
16 September 2016: Vendor validated vulnerabilities.
19 September 2016: Vendor send mitigation plan and release dates.
14 October 2016: Vendor released a new version.
15 October 2016: Public disclosure

